| Overview |
 |
Social engineering attacks are aided and abetted by Social Media: In short, what you posted to Facebook, Linked-In, and other websites can make you a target.
In the Exploit Demo section of this page you will find 5 screenshots that, in total, lead to more than 20,000 IT professionals in the aerospace and defense industries with escalated administration privs.
These people are advertising the following:
- I work in the defense aerospace industry
- Here is my name and a way to contact me
- Here is the name of the company where I have a badge, and at least one userid and password that has escalated administration privileges
- Here is the location where I where I have escalated privilege access
- Here is a list of my skills from which you can come to reasonable conclusions about the type of systems I can access
We are not suggesting everyone drop all of their social media accounts, though all of us have dropped Facebook and Twitter.
What we are suggesting is that you continue to read the material on this page and learn what you need to do to mitigate some of the risk. |
|
| |
| Exploit Demo |
Search for Network Admins in Aerospace Defense = 6,265 results
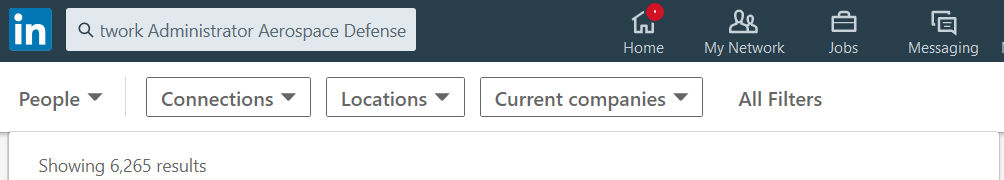
Search for System Admins in Aerospace Defense = 13,104 results
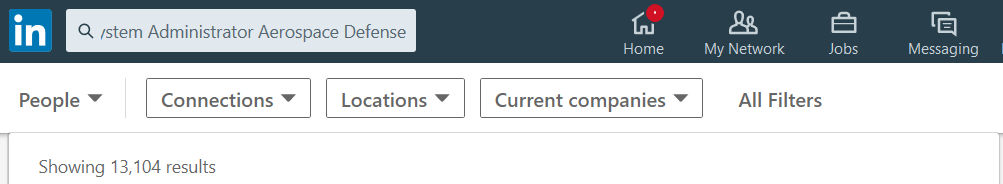
Search for Oracle Database Admins in Aerospace Defense = 700 results
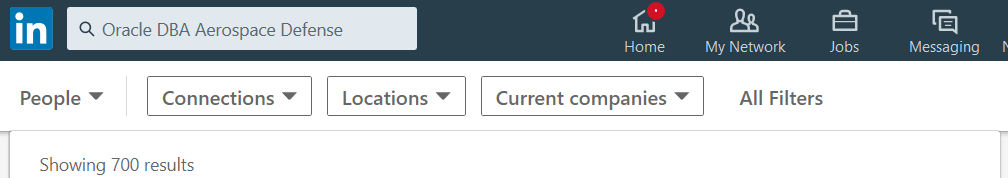
Search for a single company in Aerospace Defense = 542 followers
Experience posting for one person found with the above search
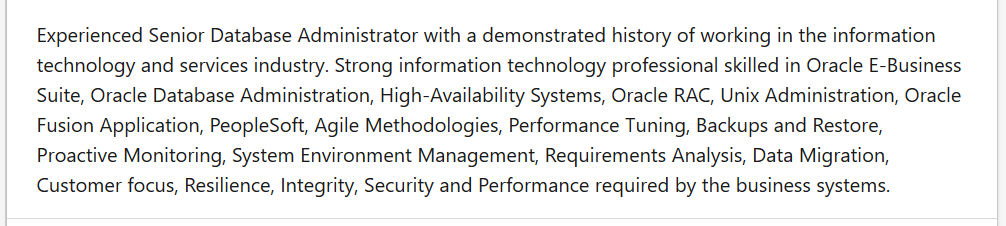
|
In the above screen captures you see how you can easy it is to set yourself up as a high value target for phishing: Likely you already have.
The first thing you must do is look in the mirror and acknowledge that you are, to some extent, advertising to people you do not know who you are, where you work, that you have a badge and access credentials that come with increased responsibilities.
We are not saying that the person working on the loading dock mustn't also be vigilant. They are, after all, giving boxes full of backup tapes to someone that drives up in a truck.
But we are saying that you likely have access to multiple systems, VPN access to the network, an MFA token generator, and you likely know where the most valuable information is stored, which databases, which schemas, which table, which columns.
You also know the protection level if any ... for example is Transparent Data Encryption in use.
Survey after survey of Network, System, and Database Administrators have shown that no one gets job-specific security training. Most IT specialists will concede that the level of IT security training they have received in their career consisted of something like this:
| "Do not click on an email link from a Nigerian prince offering you money to help him get his money out of his country" |
If you were that naive you would never have been hired to work in IT so the advice is worthless.
So you must accept the following:
- State actors (governments) and organized crime families have reason to target you
- You have an increased level of responsibility to be careful because of the target on your back
Social media is not a contest to see who can get the most connections. We recommend you go through all of your connections for all of your social media and follow the advice in the bullet-list below:
- Determine whether you know the person?
- Ask yourself whether this person has any relevance to your personal life or career? Is it a complete stranger in another country? Someone you bumped into at a conference 2 years ago?
- Drop the connection if you do not know the person, do not remember the person, cannot remember why you linked to them.
If you have questions feel free to contact us. All questions and response will be kept strictly anonymous and confidential. |
After you have taken the above steps make the following change to how you interact with people that contact you.
Phone Calls Received:
- Do you unequivocally recognize the voice or the phone number?
- If not ask for their name, location, and contact information and tell them you will return their call in a few minute
- Keep the number they provided but NEVER, EVER, call them back on
that number!
- Find an independent means of getting a phone number of their
organization:
- Check your email directory
- Call your company's HR or security department
- Find the number in email correspondence
- Find the number on the internet on a page your browser flags as trusted
- Ask a personal friend or colleague
- If on the phone you are asked a question that seems inappropriate tell the person something crashed and needs your immediate attention and ask them to send their questions in an email
Text Messages Received:
- Even if you know the person that texted you: If you are asked for any information that could be used to compromise a system, for example IP address or credentials do not respond
- Walk over to their desk and verify the request
- Verify the request by calling them on a phone number you already know and trust
- Email them
- Take the matter of confidential information being requested by text message to your manager or CISO
Email Received:
- Never click on any link ... even if it comes from your mother. Chances are your mother does practice IT security as a profession
- Highlight the link and copy it to a text editor like notepad where you can examine every character
- After verification ... manually type it into your browser
- If it is too long and complex to type in use a search engine to find the material independently (or) just forget it and get back to work
- Never respond to an email from anyone you do not personally know, or cannot validate, that asks for any information, no matter how innocuous it may seem about where you work, what you do, or for information about practices, policies, credentials or systems
If you haven't done so before check out this website and what they sell: https://discoverorg.com/
Ask yourself one simple question: How did they get the information they are selling?
Bet you they didn't send an email to your CEO and ask for it. |
| |
| Conclusion |
Social engineering exploits work because they take advantage of human nature. We tend to trust people we do not know because they have never tried to deceive us. Your position of responsibility in IT dictates that you change that behavior.
Here's an example of a telephone exchange between a principal at DBSecWorx and American Express to illustrate the point.
AEx: "Hi, this is the fraud department at American Express and we have an alert on your account."
DAM: "I'm sorry you must have a wrong number ... I don't have an American Express Card."
AEx: "Is this Daniel Morgan?"
DAM: "I'm sorry but you really do have a wrong number ... sorry I cannot help you."
The next thing Morgan did was open his wallet, pull out his American Express card, call the phone number on the back, and ask for the Fraud Department.
Critically important to the exchange is that DAM not only told the party they had a wrong number but that he denied even having an American Express card.
Had the call been fraudulent the caller would have been able to confirm that a specific person with a specific phone number had an AmEx card. Not an efficient means of theft ... but, perhaps, aimed at someone with a very large target on their back.
The call was absolutely valid, he has just tried to purchase a plane ticket at an airport in La Serena Chile for a flight back to Santiago. But there was absolutely no reason to trust an unknown caller from an unknown phone number was safe.
There was every reason to believe the number on the back of the credit card was. |





